Download the IIS 6 Resource Kit and use a tool called SelfSSL.exe. Using this tool, you can create a self signed certificate, whose is exportable, and whose common name can be anything we want. For example, to create a self signed certificate for the RDS farm called farm1.ash.local, you would run this command (make sure to start your command console with elevated privileges!):
C:\Program Files (x86)\IIS Resources\SelfSSL>selfssl /N:cn=farm1.ash.local /K:2048
Microsoft (R) SelfSSL Version 1.0
Copyright (C) 2003 Microsoft Corporation. All rights reserved.
Do you want to replace the SSL settings for site 1 (Y/N)?y
The self signed certificate was successfully assigned to site 1.
Then when you look in the computer certificates store, you will find the certificate under the personal store:

Note: You can run SelfSSL on a Windows 7 machine.
The private key is exportable, as shown by the little key located in the upper left hand corner of the certificate icon. This means you can move it to another server.
Next you need to export the certificate so you can import it to all of your RD Session Host servers in the farm:
1. Right click on the certificate and choose All Tasks —> Export….
2. As you run through the Export Certificate Wizard, make sure to choose to export the private key.
3. Enter a password for the file for security, and save the resulting .PFX file.
Now you need to import the self signed certificate to your RD Session Host server farm members. On each member:
1. open the computer certificates MMC, right click on the Personal store/Certificates folder, and choose: All tasks —> Import…
2. This starts the Import Certificate Wizard.
3. browse to the PFX file you created earlier.
4. Make sure the file extension dropdown box is set to All Files, and then choose your file and click Open.
5. Enter the password
6. install the certificate to the personal store (it is chosen by default)
7. Click Finish.
Now you have a self signed certificate that contains the farm name on all of your farm members, so you can test farm access now without getting a message that the machine you specified in RDC was not the name of the responding server.
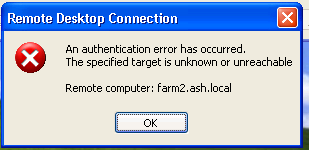
Now, you also have to install the self signed cert into the Trusted Root Certification Authorities / Certificates folder in the Computer Certificate Store, on every computer you will connect to the farm with. If you don’t you will get this error:

In a real life situation, you would purchase an SSL certificate from a public CA that is part of the Microsoft Root Certificate Program (http://technet.microsoft.com/en-us/library/cc751157.aspx) so the CA certificate used to sign the SSL certificate would automatically be downloaded to the computer Trusted Root folder via Windows Updates.
But in a test situation, you have to do this part for yourself, since your self signed certificate is not part of this program.